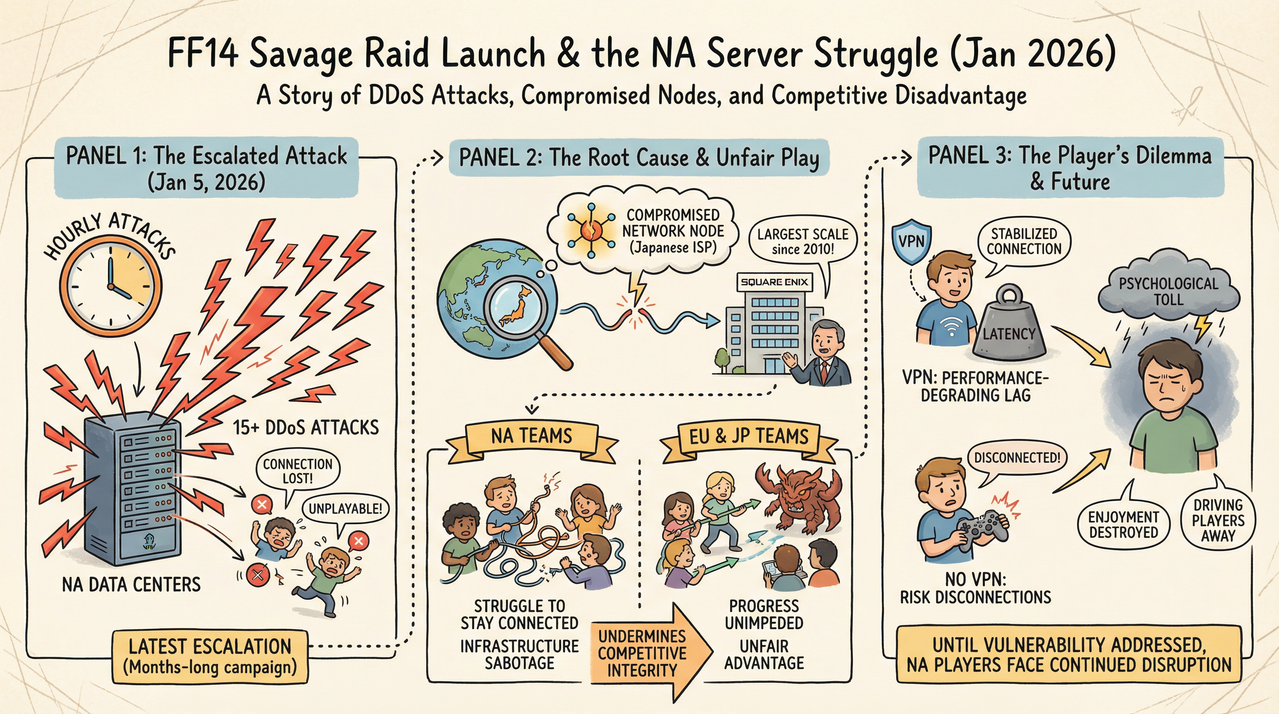
Final Fantasy 14 suffered over 15 distributed denial of service attacks in a single day on January 5, 2026, coinciding with the release of Dawntrail’s Savage raid tier. The coordinated attacks began around 2 AM PST and continued approximately every hour throughout the day, primarily targeting North American servers on the Aether, Primal, Crystal, and Dynamis data centers. Players attempting high-level Savage content found the game essentially unplayable as disconnections happened mid-combat, wiping raid groups and destroying progress in the competitive world-first race to clear new endgame content. Square Enix confirmed the attacks on the Lodestone, stating they’re investigating and implementing countermeasures, though the situation represents an escalation of DDoS problems that have plagued NA servers since October 2025.
The timing couldn’t be worse for NA players. Savage raids represent the second-highest difficulty tier in Final Fantasy 14, with world-first race competition between regions being a major community event. European and Japanese servers remained largely unaffected, giving those players significant competitive advantages as NA teams struggled to stay connected long enough to learn mechanics. Reddit user DragonEmperor reported that attacks occurred “approximately every hour, and even more often at times,” making the game “largely unplayable as soon as players entered the raids.” Some desperate NA players attempted migrating to Oceania servers to escape the attacks, but OCE data centers soon experienced similar issues as the attacker targeted them as well, though not to the same severity as NA infrastructure.
What Are Savage Raids and Why This Matters
Savage difficulty raids sit between Normal mode casual content and Ultimate difficulty encounters as Final Fantasy 14’s primary endgame for hardcore players. These eight-player raids feature complex mechanics requiring precise coordination, with world-first races being highly competitive events where teams stream progression attempts for audiences watching multiple regions compete simultaneously. The Heavyweight Savage raid tier released on January 5 represents Dawntrail expansion’s latest endgame challenge, delayed from holiday season to avoid vacation conflicts and give players time to prepare.
World-first races matter because they showcase skill, strategy, and execution at the highest level. Teams spend weeks theorycrafting optimal compositions and strategies before launch, then race against global competition to clear content first. NA teams historically compete well against European and Japanese counterparts, making these attacks particularly frustrating since they artificially handicap one entire region. When NA players disconnect mid-pull during crucial progression attempts, they lose time learning mechanics while EU and JP teams progress unimpeded, creating unfair competitive disadvantages that undermine the integrity of the world-first race.
The attacks also affect casual players attempting to enjoy new content. Savage raids aren’t exclusively for world-first competitors; thousands of players participate for fun, challenge, and rewards without caring about race placements. Disconnecting repeatedly while learning fights creates frustration that drives players away from content they’d otherwise enjoy. Eurogamer noted that this Savage launch “is not the first instance of such troubles affecting Final Fantasy 14,” pointing out that NA servers faced similar attacks just two weeks prior, suggesting a pattern of targeted harassment during major content releases.
The Infrastructure Vulnerability
PC Gamer’s coverage explains that Final Fantasy 14’s NA server issues stem from “a service provider’s wonky nodes” rather than Square Enix’s physical servers themselves. Reddit user ItinerantSoldier elaborated: “The physical servers in North America were recently improved, but the issue lies with a particular node utilized by a high-tier ISP they have an agreement with in Japan. This node is notably fragile and susceptible to DDoS attacks.” For over a year, attackers have exploited this specific vulnerability, with attack intensity fluctuating but never fully disappearing.
This network node weakness creates a bottleneck where targeted attacks disrupt service even when Square Enix’s actual game servers function perfectly. Players using VPNs that route around the compromised node report fewer disconnections, supporting the theory that the problem exists in networking infrastructure rather than game servers. Reddit user WaltzForLilly explained: “Users employing VPN services that circumvent this node have reported fewer disconnections. This was the case during earlier attacks.” However, VPNs introduce latency that high-level raiders want to avoid since frame-perfect execution becomes harder with increased ping.

Timeline of Escalating Attacks
The January 5 attacks represent escalation rather than isolated incident. Final Fantasy 14 has faced DDoS problems intermittently since the game’s original 2010 launch, with notable attack waves in 2017, 2022, and 2024. However, the current campaign beginning October 2025 represents sustained harassment rather than brief disruptions. Military.com reported attacks starting November 3, 2025, that were “temporarily mitigated before firing back up again late on Tuesday, November 4.” The attacks continued throughout December, intensifying during the holiday season and reaching peak frequency on January 5’s Savage launch.
Director Naoki Yoshida addressed the situation during a Letter from the Producer livestream in May 2024, calling earlier attacks “the largest scale seen since the game’s original 2010 launch.” PC Gamer quoted Yoshida acknowledging that attacks “have been happening since the release of DT [Dawntrail], but it has intensified since the end of summer.” These statements establish that the problem predates the current escalation, with attackers maintaining pressure for months rather than conducting isolated strikes.
Square Enix’s Lodestone posts document the relentless pace. A January 6 post confirmed “technical difficulties due to a DDoS attack,” following similar posts on January 1 and throughout December. Each announcement promises investigation and countermeasures, but the attacks continue unabated, suggesting either the attacker adapts faster than Square Enix can implement defenses or the underlying infrastructure vulnerability can’t be fixed without replacing networking agreements with Japanese ISPs.
Why NA Servers Specifically
The attacks predominantly target North American data centers, with European and Japanese servers remaining stable. This regional specificity suggests deliberate targeting rather than opportunistic attacks hitting whatever’s vulnerable. Several theories explain why NA infrastructure suffers disproportionately. First, the compromised network node exists in the routing path specifically for NA traffic, creating a chokepoint that doesn’t affect EU or JP routing. Attackers identified this weakness and exploit it repeatedly because it works.
Second, some players speculate competitive motivations drive the attacks. If attackers want to disrupt world-first races, targeting NA servers handicaps strong competition while leaving their preferred region unaffected. This theory remains unproven conspiracy but explains the timing correlation between major content releases and attack intensity. Reddit user The25thDivisionOf2 noted: “Experiencing 15 drops in a single day coinciding with the release of Savage likely indicates a targeted DDoS attack. This behavior differs significantly from the ongoing network problems we’ve been facing.”
Third, real-money trading ban waves might motivate revenge attacks. Reddit user ProtoMan0X suggested attacks “began around the time of a banwave targeting real money trading, which led many to believe it was a response to that.” RMT operations that got banned could be retaliating by disrupting service, though this theory struggles to explain why attacks continue months after ban waves or why NA infrastructure specifically gets targeted if RMT operations exist globally.
The Platform Difference
Reddit user PraxisV noted that “PS5 users are less impacted” by the attacks compared to PC players. This platform difference suggests the DDoS targets specific connection methods or routing paths used predominantly by PC players. Whether this reflects VPN usage being more common on PC, different networking protocols between platforms, or routing variations depending on how PlayStation Network traffic flows versus direct PC connections remains unclear. The distinction matters because it indicates potential workarounds exist if players understand what makes PS5 connections more resilient.
Some PC players report that connecting through VPNs improves stability by routing around the compromised node. However, VPN usage introduces latency that degrades performance for high-level content requiring precise timing. The trade-off between stable connections with worse ping versus unstable connections with better ping creates impossible choices for competitive raiders who need both reliability and responsiveness. Yahoo Tech quoted Reddit user Lindaru noting “It only US that are affected, while JPN/EU servers remain fine, which is quite strange,” emphasizing how regionally isolated the problem remains.
Square Enix’s Response
Square Enix consistently acknowledges attacks through Lodestone posts but provides minimal detail about countermeasures or timelines for resolution. The January 6 statement reads: “We are currently facing technical difficulties due to a DDoS attack. Players may encounter various issues because of this. We are investigating the attack and implementing countermeasures. Further updates will be provided as the situation evolves.” This language mirrors previous statements from November and December attacks, suggesting either limited progress on permanent solutions or deliberate vagueness to avoid revealing defensive strategies to attackers.
Director Yoshida emphasized during May 2024 livestreams that Square Enix’s infrastructure team works around the clock employing “both internal and external resources to devise strategies to counteract the attacks.” He acknowledged complexity: “The attacks themselves are relatively simple, involving hacked computers sending packets to the servers. However, the team is working diligently to implement the necessary countermeasures.” This admission reveals the fundamental challenge of DDoS mitigation, where simple attacks require complex defenses and attackers adapt faster than defenders implement protections.
The improved NA server infrastructure deployed in recent years allows faster recovery according to Reddit discussions. When attacks knock servers offline, technicians can “change the physical server location and restart it within just a few minutes,” reducing downtime compared to older infrastructure. However, faster recovery doesn’t prevent attacks, just minimizes their duration. Players still disconnect, lose progression, and face repeated disruptions even if individual outages last minutes rather than hours.

Impact on Player Experience
The human cost of these attacks extends beyond statistics about disconnected players. Reddit user HellaSteve mentioned “experiencing disconnections three times within a half-hour of the new Savage content becoming available,” capturing the frustration of repeated failures through no fault of their own. Yahoo Tech reported that “several players are reporting that the Savage encounters are currently unplayable due to persistent connection problems, which prevent them from maintaining a stable connection long enough to engage in the fights.”
For world-first race competitors, these attacks destroy months of preparation. Teams spend weeks theorycrafting strategies, optimizing gear, and coordinating schedules to attempt progression immediately at launch. When infrastructure failures prevent executing those plans, the time investment becomes wasted effort through circumstances completely beyond player control. Even teams that successfully stay connected face disadvantages since practice time lost to disconnections means less experience with mechanics compared to regions with stable servers.
Casual players attempting Savage content for fun face equal frustration despite lacking competitive aspirations. Learning complex mechanics requires consistent attempts to recognize patterns and practice execution. When disconnections interrupt learning, retention suffers and progression slows dramatically. The psychological impact of knowing you might disconnect at any moment during a 10-15 minute encounter creates anxiety that undermines enjoyment even during successful attempts that complete without issues.
The Broader MMO Context
Final Fantasy 14’s DDoS problems exist within broader MMO industry challenges around infrastructure and security. No major online game is immune to DDoS attacks; World of Warcraft, Guild Wars 2, and other MMORPGs face similar issues periodically. However, the sustained nature of FF14’s current campaign stands out. Most DDoS attacks last hours or days before attackers lose interest or defenders implement effective countermeasures. FF14’s attacks persist for months with escalating intensity during major content releases, suggesting unusual motivation or resources behind the campaign.
The compromised network node situation highlights how games rely on infrastructure beyond developer control. Square Enix can perfect their server code but remains vulnerable to problems in networking agreements with ISPs and routing through third-party nodes. Fixing these issues requires coordinating with multiple organizations across countries with different legal jurisdictions and business priorities. Even when Square Enix identifies problems, implementing solutions depends on ISP cooperation and timeline commitments from partners who view one gaming company’s complaints as low priority compared to broader business concerns.
The attacks also raise questions about attacker motivations and consequences. DDoS attacks are illegal in most jurisdictions but prosecuting perpetrators requires identifying them, which proves difficult when attacks route through compromised computers distributed globally. Even when authorities identify attackers, jurisdictional issues complicate prosecution if perpetrators operate from countries without extradition treaties or where cybercrime receives low enforcement priority. This practical immunity emboldens attackers who face minimal consequences for disrupting services affecting hundreds of thousands of players.
FAQs About FF14 DDoS Attacks
How many DDoS attacks hit Final Fantasy 14 on January 5, 2026?
Over 15 DDoS attacks hit Final Fantasy 14 in a single day on January 5, 2026, starting around 2 AM PST and continuing approximately every hour throughout the Savage raid launch. The attacks primarily targeted North American data centers, making the game largely unplayable for NA players.
Why are only NA servers affected by FF14 DDoS attacks?
NA servers route through a compromised network node with a Japanese ISP that’s vulnerable to DDoS attacks. European and Japanese servers use different routing paths that don’t go through this weak point. Players using VPNs that bypass the compromised node report fewer disconnections, confirming the infrastructure issue.
How long have FF14 DDoS attacks been happening?
The current wave of attacks began in October 2025 and intensified through November-December before reaching peak frequency during the January 5, 2026 Savage raid launch. However, FF14 has faced DDoS attacks intermittently since 2010, with major waves in 2017, 2022, and 2024.
What are Savage raids in Final Fantasy 14?
Savage raids are challenging eight-player endgame content representing the second-highest difficulty tier in Final Fantasy 14, below only Ultimate raids. They feature complex mechanics requiring precise coordination and host competitive world-first races between regions when new tiers release.
Can VPNs help avoid FF14 DDoS disconnections?
Yes, players using VPNs that route around the compromised network node report fewer disconnections. However, VPNs introduce latency that degrades performance for high-level content requiring precise timing, forcing players to choose between stable connections with worse ping or unstable connections with better ping.
Why do DDoS attacks target Savage raid launches?
Attacks during major content releases maximize disruption impact during the competitive world-first race and when player engagement peaks. Whether this reflects deliberate targeting to handicap NA teams, revenge from banned RMT operations, or opportunistic timing remains unconfirmed, though the correlation appears deliberate.
What is Square Enix doing about FF14 DDoS attacks?
Square Enix acknowledges attacks through Lodestone posts and states they’re investigating and implementing countermeasures. Director Yoshi-P confirmed the infrastructure team works around the clock with internal and external resources, though the compromised network node issue requires ISP cooperation Square Enix can’t directly control.
Are PS5 players affected by FF14 DDoS attacks?
PS5 players report being less impacted than PC players, suggesting the attacks target specific connection methods or routing paths used predominantly by PC. The platform difference indicates potential workarounds exist, though the exact reason for PS5’s resilience remains unclear.
Conclusion
Final Fantasy 14’s 15+ DDoS attacks during the January 5, 2026 Savage raid launch represent the latest escalation in a months-long campaign that’s made North American servers increasingly unplayable during peak content releases. The coordinated hourly attacks targeting NA data centers during the competitive world-first race create unfair disadvantages where European and Japanese players progress unimpeded while NA teams struggle to stay connected long enough to learn mechanics, undermining competitive integrity through infrastructure sabotage rather than skill differences. Square Enix’s acknowledgment that the problem stems from a compromised network node with a Japanese ISP reveals the fundamental challenge: even perfect server code can’t defend against vulnerabilities in third-party infrastructure outside direct developer control, requiring coordination with ISPs who may view one game’s complaints as low priority compared to broader business concerns. Director Yoshida’s May 2024 statement calling these attacks the largest scale since 2010 launch establishes the severity, while the sustained nature of attacks from October through January suggests unusual motivation or resources behind the campaign compared to typical DDoS harassment that lasts days not months. For NA players, the situation creates impossible choices between using VPNs that stabilize connections but introduce performance-degrading latency or playing without VPNs risking disconnections at crucial moments. The psychological toll of knowing you might disconnect during any 15-minute encounter regardless of skill or preparation destroys enjoyment even during successful attempts, driving players away from content they’d otherwise love. Until Square Enix and their ISP partners address the underlying network vulnerability, NA players face continued disruption during every major content release when attacker motivation peaks and player frustration matters most.

