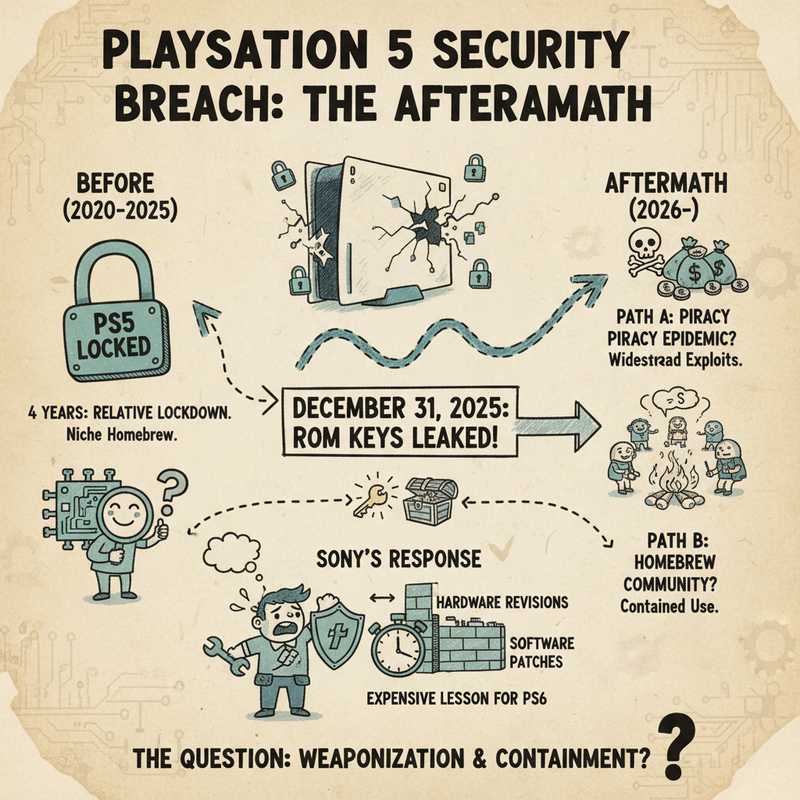
Sony kicked off 2026 facing a security crisis that could haunt the PlayStation 5 for the rest of its lifecycle. On December 31, 2025, the console’s BootROM keys were publicly dumped online and spread across developer wikis and forums. This isn’t just another software vulnerability that Sony can patch in the next system update. These are hardware-level cryptographic codes burned directly into every PS5’s processor chip, making them effectively unpatchable on consoles already sold.
What Actually Leaked and Why It Matters
The leaked data contains Level 0 BootROM keys for the PlayStation 5. When you press the power button on your console, the CPU immediately runs code stored in read-only memory called the BootROM. This code uses cryptographic keys to verify that the bootloader hasn’t been tampered with before allowing the system to continue starting up. Think of it as the first security checkpoint that every PS5 must pass through before it can do anything else.
Now that these keys are public knowledge, hackers and homebrew developers can decrypt the PS5’s bootloader and study exactly how Sony’s boot security system works. The complete list of bootloader ROM keys is already available on the PS5 Developer Wiki, including hex strings and keyseeds. Anyone with the technical knowledge can now access the hardware-level secrets that have kept the PS5’s security largely intact since its November 2020 launch.
Why Sony Can’t Just Update This Away
Here’s the brutal reality for Sony: these keys are physically etched into the silicon of the PS5’s custom AMD APU during manufacturing. ROM stands for Read-Only Memory, and that’s exactly what it means. Sony cannot change these keys through a firmware update because the hardware BootROM still expects the original keys to verify the bootloader. Any attempt to change the software-level keys without matching hardware would simply cause affected consoles to fail during the boot process.
According to cybersecurity analysts at The Cyber Sec Guru, this represents an unpatchable problem. The only real solution would be for Sony to manufacture entirely new APUs with different ROM keys for future production runs. Every PS5 Standard Edition, Digital Edition, and Pro model currently in homes worldwide remains permanently vulnerable to whatever exploits emerge from this leak. We’re talking about roughly 65 million consoles that Sony sold through September 2025, all carrying the same compromised keys.
What This Enables For Developers and Hackers
It’s important to understand that this leak doesn’t automatically result in widespread PS5 jailbreaks appearing tomorrow. Sony has multiple layers of security beyond the BootROM, and those will need to be bypassed before we see fully functional custom firmware. However, the ROM key leak removes one of the most significant barriers and provides crucial information that makes every subsequent security layer easier to attack.
Until now, PS5 hackers have focused on attacking the kernel or exploiting the WebKit browser, which are software-level vulnerabilities that Sony routinely patches. The ROM keys change the entire landscape. Developers can now decrypt the Level 1 Bootloader and understand the PS5’s boot chain at the hardware level. This knowledge accelerates the development of homebrew applications, custom firmware, and potentially enables running unauthorized software including game backups.
Tom’s Hardware reports that while you won’t get a jailbroken PlayStation 5 overnight from this leak alone, it significantly lowers the barrier for those working on compromising the console. The Cyber Sec Guru anticipates we’ll see more sophisticated game backups and custom loaders appearing throughout 2026, and that this leak drastically shortens the timeline for mass piracy becoming feasible on the platform.
The PS3 Nightmare All Over Again
Sony has lived through this scenario before with catastrophic results. The PlayStation 3 suffered a similar fundamental security compromise when hackers discovered cryptography mistakes that allowed custom firmware installation. This led to rampant piracy, widespread online cheating in multiplayer games, and years of Sony playing whack-a-mole trying to ban offenders and patch new exploits as they emerged.
The company became infamous for its aggressive response to PS3 hacking, including the high-profile lawsuit against hacker George Hotz in 2011 for leaking PS3 encryption keys. Sony eventually settled with a permanent injunction preventing Hotz from circumventing any Sony product security. They also implemented permanent console bans from PlayStation Network for anyone caught running custom firmware or modified system software, a policy that continues today.
What Happens Next
For average gamers playing legitimately purchased games, nothing changes immediately. Your PS5 works exactly the same today as it did before New Year’s Eve. However, over the coming months and years, this leak creates several concerning possibilities. The most obvious threat is piracy. If developers successfully create methods to run unsigned code on the PS5 using these ROM keys, it could enable playing unauthorized game copies without Sony’s verification.
Online cheating represents another major concern. Custom firmware could potentially allow players to manipulate game data in ways that provide unfair advantages in competitive multiplayer. Sony would likely respond with permanent console bans from PlayStation Network, similar to their PS3-era tactics. Getting banned means losing access to online multiplayer, the PlayStation Store, cloud saves, and essentially every online feature that makes modern consoles useful.
The Homebrew Perspective
Not everyone interested in console modification is a pirate or cheater. The homebrew community develops legitimate applications, emulators, media players, and quality-of-life improvements that manufacturers don’t officially support. Some developers want the ability to run Linux on their PS5, create custom themes, preserve older games through emulation, or develop indie software without Sony’s approval process.
The ROM key leak could eventually enable these legitimate use cases. However, they come bundled with the same risks. Sony doesn’t distinguish between homebrew developers running custom software for educational purposes and pirates stealing games. Any console detected running modified firmware faces the same permanent ban regardless of intent.
Sony’s Limited Response Options
Sony’s choices for addressing this crisis are extremely limited and mostly unpleasant. They can’t patch the existing hardware through software updates. A full console recall would cost billions of dollars while creating a public relations disaster. The most realistic scenario involves Sony quietly introducing a hardware revision with new APUs for future manufacturing, similar to Nintendo’s response when the Switch Tegra exploit was discovered.
For the 65 million consoles already sold, Sony will likely focus on software-side detection methods and aggressive PSN enforcement. They may accelerate requirements for always-online verification and server-side checks to make piracy less attractive even if working exploits emerge. The company will also probably increase monitoring for suspicious activity and issue ban waves targeting any consoles detected running modified software.
Some analysts suggest Sony could offer a motherboard replacement program for concerned users, though this seems unlikely given the massive cost and logistics involved. The company would essentially need to replace the core component of every PS5 currently in circulation, a task that makes even Apple’s largest recall programs look manageable by comparison.
Frequently Asked Questions
Can I jailbreak my PS5 right now with this leak?
No. The ROM key leak is a significant piece of the puzzle but doesn’t automatically result in working jailbreaks. Hackers still need to develop exploits that leverage these keys to bypass Sony’s other security measures, which could take months or years.
Will my PS5 still work normally after this leak?
Yes, your console functions exactly as before. This leak doesn’t affect normal operation. It only provides tools for developers to potentially create jailbreaking methods in the future.
Can Sony fix this with a system update?
No. The ROM keys are burned directly into the hardware at the chip level. Sony cannot change them through software updates without causing every affected PS5 to fail during boot. The only fix is manufacturing new hardware with different keys.
Which PS5 models are vulnerable to this leak?
All current PlayStation 5 models are potentially affected, including the standard edition, digital edition, and PS5 Pro. Any console manufactured before Sony implements a hardware revision with new ROM keys carries this vulnerability.
What happens if I modify my PS5 when exploits become available?
Based on Sony’s past behavior with the PS3, you would almost certainly receive a permanent ban from PlayStation Network. This means losing access to online multiplayer, the PlayStation Store, cloud saves, and all online features.
Has Sony experienced something like this before?
Yes. The PlayStation 3 suffered a similar catastrophic security breach involving compromised encryption keys that allowed custom firmware installation. This led to widespread piracy and years of aggressive enforcement through ban waves and lawsuits.
Could this affect PS5 game sales or developer confidence?
Potentially. If piracy becomes widespread due to exploits built from these leaked keys, developers may hesitate to invest heavily in PS5-exclusive titles. However, this depends entirely on whether hackers successfully turn these keys into practical jailbreak tools.
Will future PS5 consoles be immune to this leak?
Likely yes. Sony will probably manufacture new APUs with different ROM keys for future production runs. However, this doesn’t help the 65 million consoles already sold that carry the compromised keys.
A Defining Moment For PS5 Security
This leak represents a fundamental shift in the PlayStation 5 security landscape. For four years, the console remained relatively locked down compared to previous generations. That era effectively ended on December 31, 2025. Whether this leads to another PS3-style piracy epidemic or remains largely contained to niche homebrew communities depends on what happens over the next several months as developers work with these newly available keys.
The gaming community now enters a waiting game. Security researchers and homebrew developers are undoubtedly analyzing these ROM keys right now, searching for ways to leverage them into working exploits. Meanwhile, Sony scrambles behind the scenes to implement hardware revisions and strengthen software-level detection before the situation spirals out of control. One thing is absolutely certain: Sony just learned a brutally expensive lesson about hardware security that will influence their approach to the PlayStation 6 and beyond. The question isn’t whether this vulnerability exists anymore. That’s confirmed. The question is how quickly and effectively it gets weaponized, and whether Sony’s response measures prove sufficient to contain the damage.


